
Introduction
In today's digital age, cybersecurity has become a critical concern for individuals, businesses, and governments alike. As cyber threats grow more sophisticated, traditional methods of detecting and mitigating these threats are often no longer sufficient. Enter machine learning—a game-changing technology that is revolutionizing the way we approach cybersecurity. By harnessing the power of machine learning, we can identify and mitigate attacks that might otherwise go unnoticed by the human eye. This is where binary classification comes into play, a fundamental machine learning technique that categorizes data into two distinct classes, such as "normal" or "malicious" traffic. In this project, we'll explore how machine learning, specifically logistic regression, can be used to detect intrusions in network traffic, providing a more efficient and accurate way to safeguard our systems.

Image Source: geeksforgeeks
Binary Classification
Binary classification is a machine learning algorithm that categorizes data into two classes, such as "0" or "1". In this case, "0" means normal traffic, and "1" means malicious traffic. It's a supervised learning method where the categories are predefined. The classification algorithm is an output of the function:
y = f(x), where y is the categorical output.
A classification algorithm would classify the dataset into either one of the two classes.
Types of Classification
- Binary: If the classification has only two outcomes.
- Multi-Class: If there are more than two outcomes.
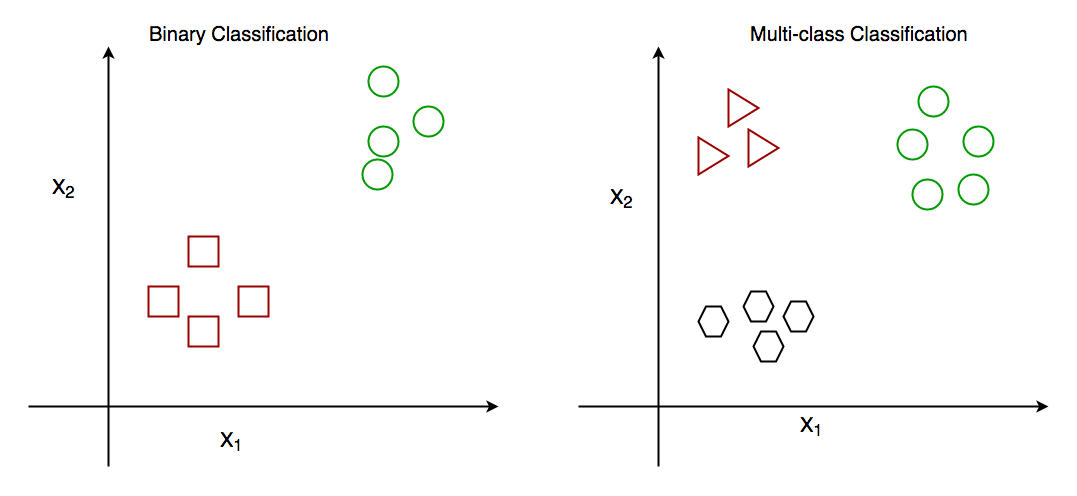
Image Source: geeksforgeeks
Evaluation of Model
Confusion Matrix
A confusion matrix is a table that shows which classifications were made correctly. It helps us understand the performance of the model by comparing the actual and predicted values.
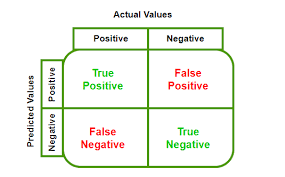
Image Source: geeksforgeeks
AUC-ROC Curves
ROC (Receiver Operating Characteristic) is a graphical representation of the confusion matrix. Instead of true positive and true negative, it shows the True Positive Rate (TPR) and False Positive Rate (FPR). AUC (Area Under Curve) is the area under the ROC curve, which shows how well the model can classify between the positive and negative classes.
AUC vs ROC: ROC shows the model's performance at various thresholds, while AUC provides a single number representing the overall performance of the model.
If the AUC score is:
- 1: The model is perfect (but may be overfitted).
- 0.9: The model is excellent.
- 0.8 - 0.9: The model is good.
- 0.7 - 0.8: The model is fair.
- Below 0.7: The model is poor and not suitable for classification.
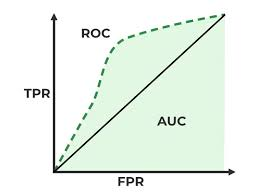
Image Source: geeksforgeeks
Intrusion Detection Using Logistic Regression
Intrusion is the process in which a malicious actor exploits vulnerabilities in a system to gain unauthorized access. Traditional methods like IDS (Intrusion Detection Systems) and IPS (Intrusion Prevention Systems) are often insufficient against modern threats. Machine learning, specifically logistic regression, can be used to classify network traffic as normal or malicious.
Why Logistic Regression?
- Simple and Interpretable: Easy to understand and implement, especially for beginners.
- Binary Classification Task: Perfect for problems with two outcomes (e.g., normal or malicious).
- Easy to Implement: Requires less tuning compared to complex models like Random Forest or Neural Networks.
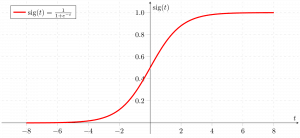
Image Source: geeksforgeeks
Dataset - The Source
A high-quality dataset is crucial for training an effective machine learning model. Here are the key aspects to consider:
- Completeness: Ensure the dataset has no missing values.
- Accuracy: Validate the correctness of the data.
- Consistency: Ensure the data format is consistent.
- Relevance: Remove irrelevant features.
- Validity: Ensure the data meets the required constraints.
- Noise-free: Remove outliers and irrelevant variations.
- Data Bias: Avoid datasets that are heavily biased toward a specific outcome.
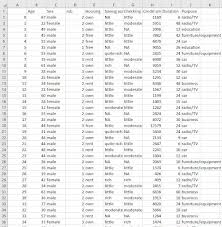
Image Source: geeksforgeeks
Wrapping up
So with this I'm wrapping up the 1st part of Applied machine learning in cybersecuriyt so feel free to contact me regarding your Queries. I may not be a wizard at this. But I know my art
● Contact Me
Get in touch
ahzaaf.ajin@gmail.com